Jatin Shankhla
Just completed Ethical Hacking course. Exclusive content totally practical based. Best choice for cybersecurity learning.
Ethical Hacking Course In Gurgaon

Days
Hours
Minutes
Seconds

✅ Hands-on Training with Real Case Studies
✅ Expert-Led Sessions by Cybersecurity Professionals
✅ Industry-Recognized Certification
✅ Career-Ready Skills for Law Enforcement & Corporate Sector
Our Six Months Diploma in Digital Forensics focuses on real-world investigation techniques, cybercrime analysis, and evidence recovery. Designed to match industry standards, the program equips you with the skills required for diverse roles in cybersecurity and digital forensics.
40+ Hours LIVE Instructor-led Training
Learn from Certified Trainers
Hands-on Practical Training
98% Exam Success Rate
Career Guidance & Mentorship
Community & Peer Support
Access to Recorded Sessions
Extended Post-Training Support
Introduction to Windows
How Binary Works
User and Permissions
Disk Management
Intro. to Task Management
Event Viewer
Network Sharing
Window Registry
Policy Editor
Batch Scripting
Creating Virus for Fun
BIOS
Virtualizations
Computer Networking
What is Networking & Its Importance in Connecting Computers?
How Internet Works?
Computer Network and Types of Network
Network Topologies
Network Components and Devices
OSI and TCP/IP Model
IP and MAC Address
IPv4 and IPv6 Packet Structure
Basics of Addressing and Subnetting
Web Server
Network Protocols + Ports
Network Services
History and Feature of Linux
Architecture of Linux OS & Linux File System
Software Package Management
Linux Tools and Arguments
User and File Permissions
Special Permission
Network Config, Logs and Text Processor Commands
File Transfer and Archiving
BASH Scripting
Types of Peripheral Devices
PC Expansion Cards
Identify Common PC Ports & Connectors Types and Associated
Storage Devices
Mother Board Components and Its Properties
LINUX
Linux System Monitoring
Analyzing and Storing Logs
Service and Process Management
Configuring and Securing Services
Introduction to Linux Server
IP Table & IP Rules
Environment Variable
Bash Scripting
WINDOWS
Shell & Kernel
Bypass Windows Password
Introduction to Programming Languages & Logics
Powershell Scripting
Internet, Intranet & Networking
Demilitarized (DMZ)
Protocol & Servers
DNS Security Extension & DHCP
Telnet & SSH
Firewall (IDS, IPS & IDPS)
VPN & Tunneling
Network Ports
Port Security
Proxy Server & Proxy Chaining
Classes of Routing Protocols
Access Control List (ACL)
VLan Trunking Protocol
Networking Address Translation (NAT & PAT)
Spanning Tree Protocol
Concept of Real-World Networks
Addressing & Subnetting
Introduction to Cisco Packet Tracer
Concept of Real World Network
Configure Your Own LAN & WAN
Cyber Laws & Legal Complexities
Hacking Lab Setup for Exploitation
Foot printing and Reconnaissance
OSINT (Open Source Intelligence)
Internal & External Network Scanning
Enumeration of System & Web App
Security Flaws Analysis – Vulnerability Assessment with Metasploit, Exploit DB and More
Malware Threats & Analysis
Password & Data Sniffing
Social Engineering Techniques
DOS – Denial of Service & DDOS Attacks
Prevention from IDS, IPS, Firewall
Hacking Web Server
HoneyPot
SQL Injection Attacks – Database Exploitation
Attacking Wireless Networks
Cloud Computing & Security
Cryptography – Art of Encryption & Decryption
Worm GPT & AI Tools in Ethical Hacking
Anonymity Unleashed: The Art of Staying Incognito
Google Dorking
Password Cracking
End Point Security
Penetration Testing: Introduction
Reconnaissance: Advanced Information Gathering
Vulnerability Analysis: Identifying the Weakness and Logical Flaws
Exploitation: Network and Other Services or Applications Exploitation
Exploitation: Gaining the Initial Access
Exploitation: Generating Malicious Payloads for Exploitation
Exploitation: Automated and Manual Exploitation of System Vulnerabilities
Mitigate the Identified Vulnerabilities and Re-testing
Exploitation: Windows Privilege Escalation – Owning the Windows Server
Exploitation: Linux Privilege Escalation – Owning the Linux Server
Post Exploitation: Compromising the Network
Post Exploitation: Pivoting and Tunneling – Access the Hidden Corners of Network Securely
Post Exploitation: Controlling the Compromised Devices using C2 Server
Reporting and Remediation
Antivirus Evasion: Bypass the Security to Deliver Payloads
Active Directory: Exploiting the Infrastructure
Penetration Testing Standards (PTES)
NIST Cyber Security Framework
Payment Card Industry Data Security Standard (PCIDSS)
Mitre & ATTCK Framework

With our Cybersecurity & Ethical Hacking training programs (Online & Offline – Gurgaon & Rohtak), we help you build the skills that transform your career and open high-demand job opportunities.

Projected to be unfilled globally by 2025, highlighting demand for Ethical Hackers.

Information Security roles are expected to grow significantly by 2030.

Seeking to hire Certified Ethical Hackers to strengthen their cybersecurity posture.
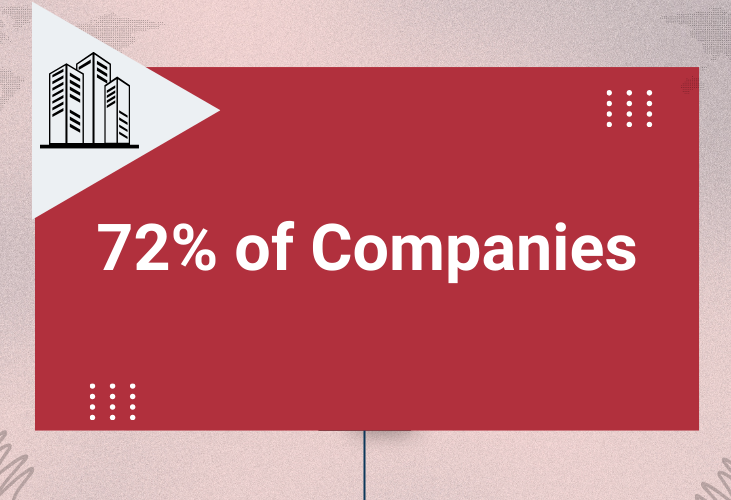
Investing in cybersecurity training for their employees to ethical hacking skills.
Our clients love our ethical hacking course in Gurgaon and cybersecurity
training in Gurgaon for its practical approach.


Just completed Ethical Hacking course. Exclusive content totally practical based. Best choice for cybersecurity learning.


Best coaching institute for cyber security. Teachers are very supportive and all facilities are provided here .


Best service provider in gurugram. Best ethical havking services and digital forensics also.


M Cyber Academy is the best service provider in the field of cybersecurity. The behavior of the staff members is supportive.


Enrolled for 1 year diploma course, perfect for a beginner to learn advance cybersecurity topics and pursue carrier in cybersecurity